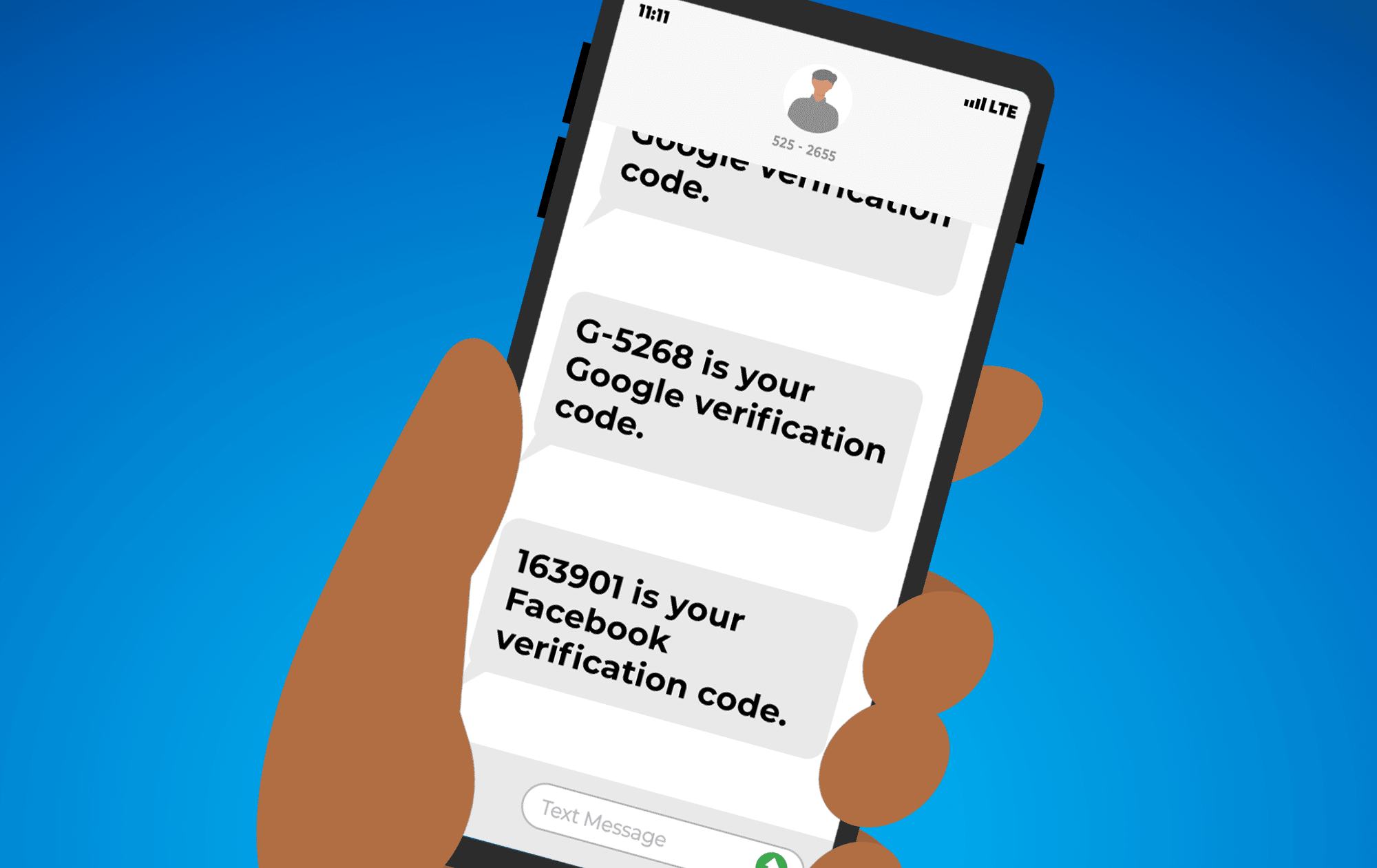
Unexpected 2FA Codes: Your Cybersecurity Wake-Up Call
We’ve all had those moments of confusion when our phone buzzes with a notification that doesn’t seem quite right. If you’ve ever woken up to a text with some random numbers and wondered what it is, you’re not alone.
Getting a code for two-factor authentication (2FA) from a service you use when you didn’t request one deserves some attention. Rather than ignoring the strange message, it’s a good idea to take action to help protect your online accounts.
Understanding 2FA
2FA, or “Two-Factor Authentication,” is an important security feature many apps and websites use. It adds an extra verification step beyond just a password. After you log in, 2FA will text or email you a special code to enter before you’re given access to your account. This acts like a second lock, keeping hackers out even if they somehow steal your password.
Spot the Warning Signs
When you receive a 2FA code you didn’t request, it’s a clear sign that someone is trying to access one of your online accounts. It often indicates that your password has been compromised through a large-scale data breach or a more targeted attack. Hackers may be attempting to log in using your stolen credentials, and the 2FA code is the only thing standing in their way.
Taking Immediate Action
Rather than ignoring the 2FA code or brushing it off, it’s important to take action right away to secure your accounts.
- Do not click on any links in the email or SMS. Open a browser, log in to the relevant account, and change your password to something unique and complex. Make sure it’s different from the one you used before and not used for other accounts.
- Check if your old password was involved in any known breaches using a tool such as HaveIBeenPwned.com. This can help you identify if you have any other accounts that may be at risk.
- Consider changing passwords for any other accounts using the same or similar passwords in case of credential stuffing attacks. This is when hackers use stolen passwords from one breach to try and access other accounts.
- Be wary of emails or texts asking you to provide a 2FA code. Legitimate services will never ask for this, and it’s likely a phishing attempt.
This unexpected 2FA code experience is a valuable reminder of the importance of proactive security measures. Two-factor authentication is what saved you this time by blocking the hacker’s attempt to access your account, so take a moment to ensure you’ve enabled it on every site that offers it.
Additionally, using unique, strong passwords for each account is essential to prevent the ripple effects of a single data breach. A password manager can help you generate and store complex credentials, ensuring one compromised password doesn’t put all your other accounts at risk.
While complete online security can never be guaranteed, taking these fundamental steps – enabling 2FA and using unique passwords – goes a long way toward safeguarding your personal information and digital identity.
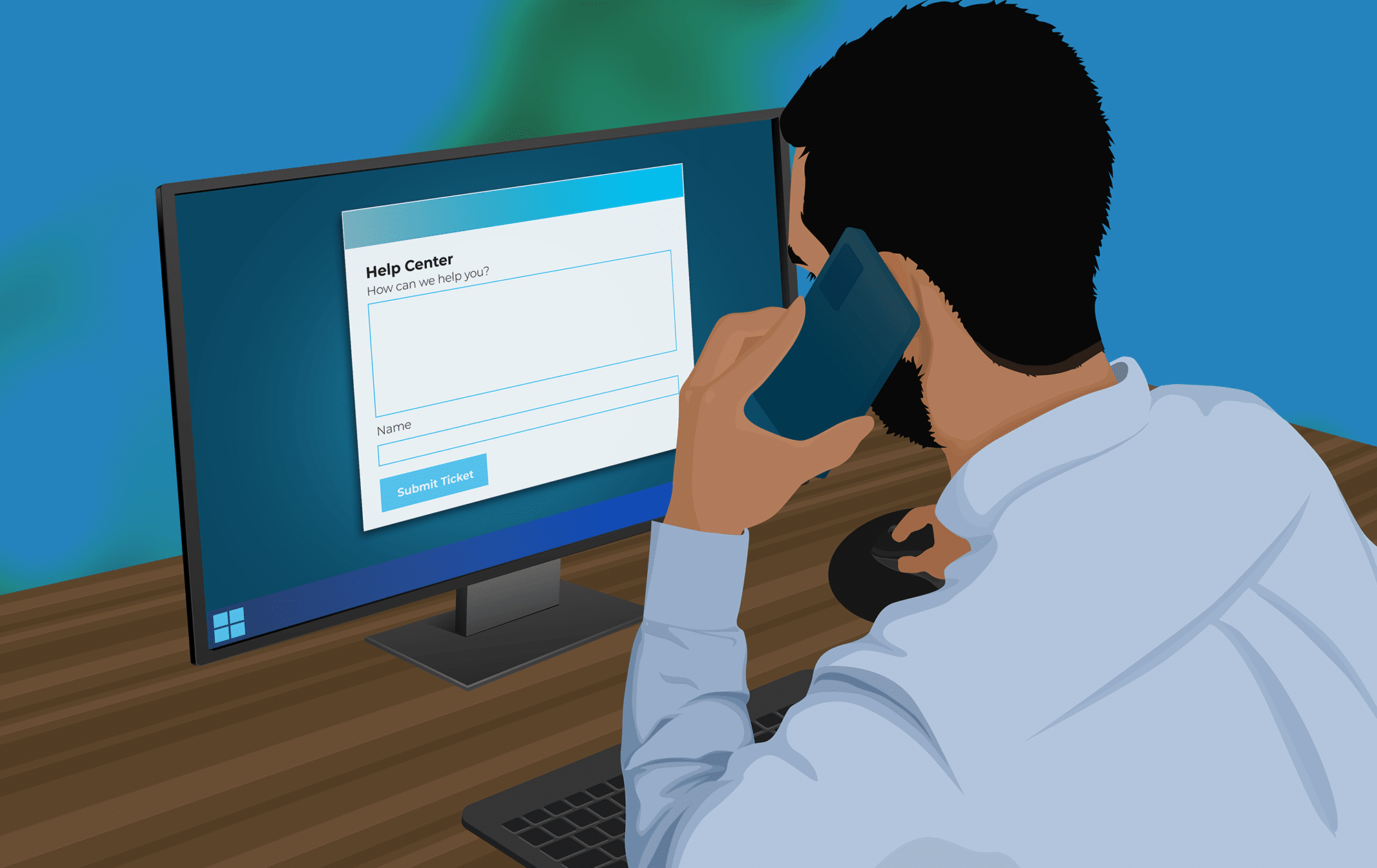
 We’ve all been there: an unexpected tech glitch throws a wrench in your works at the worst possible moment. As annoying as it is, staying calm and providing full transparency with your IT friends will have you back up and running in no time.
We’ve all been there: an unexpected tech glitch throws a wrench in your works at the worst possible moment. As annoying as it is, staying calm and providing full transparency with your IT friends will have you back up and running in no time.
 If your trusty office PC has started showing its age, with more issues cropping up lately, you may be wondering if it’s finally time to say goodbye to your old friend. Or could some TLC in the form of repairs get it back in the game?
If your trusty office PC has started showing its age, with more issues cropping up lately, you may be wondering if it’s finally time to say goodbye to your old friend. Or could some TLC in the form of repairs get it back in the game?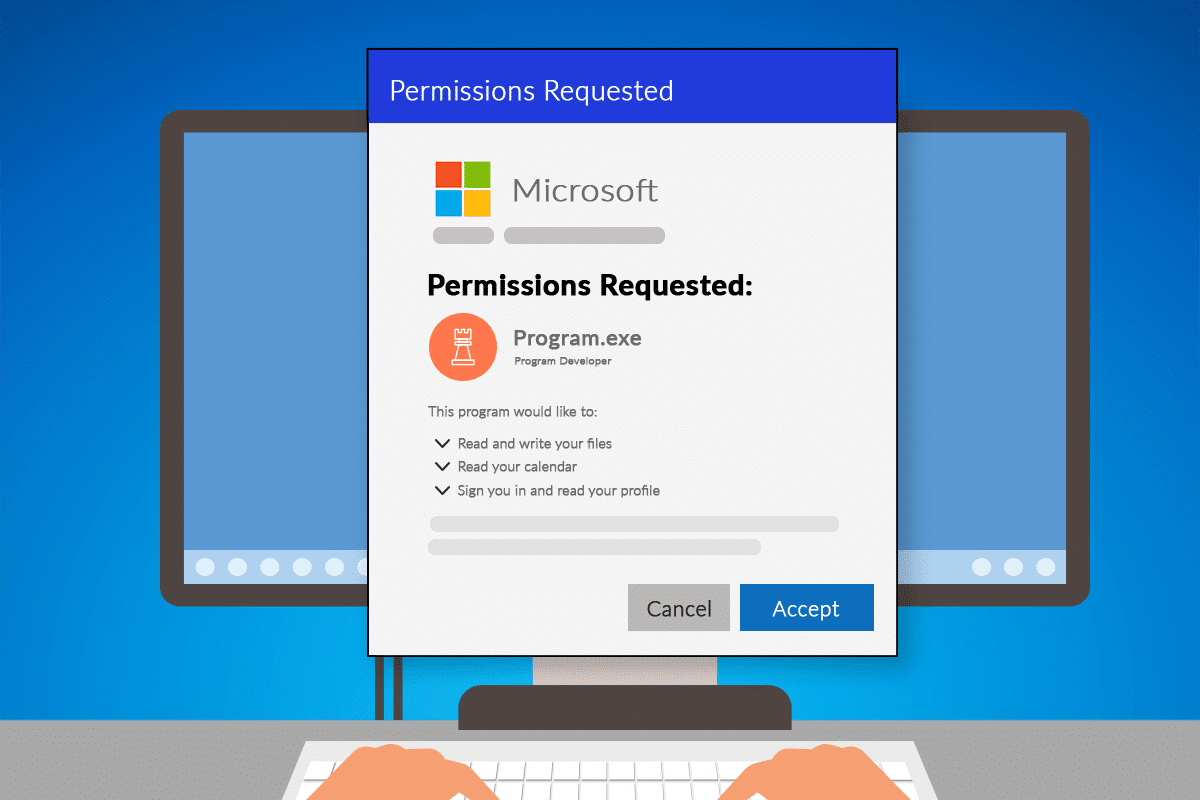
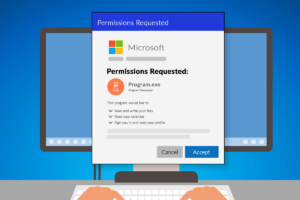 If your business uses Microsoft 365 applications, you or your employees may have encountered a pop-up window requesting permission to access various account data.
If your business uses Microsoft 365 applications, you or your employees may have encountered a pop-up window requesting permission to access various account data.
 It’s a Wednesday afternoon, and you’ve just sat down to focus on an important project. But suddenly, you notice your internet connection isn’t working. A few minutes later, the printer on the other side of the office starts beeping with an error. Then, a pop-up appears on your computer saying your antivirus subscription needs to be renewed.
It’s a Wednesday afternoon, and you’ve just sat down to focus on an important project. But suddenly, you notice your internet connection isn’t working. A few minutes later, the printer on the other side of the office starts beeping with an error. Then, a pop-up appears on your computer saying your antivirus subscription needs to be renewed.



