Why Businesses Should Never Use Consumer-Grade Hardware or Software
 If you run a business, the technology you choose matters more than you might think. It’s tempting to save money by picking up consumer-grade laptops, routers, and software, but this decision often backfires. What works fine for home users can cause major headaches in a business setting, leading to security risks, unexpected downtime, and higher costs in the long run.
If you run a business, the technology you choose matters more than you might think. It’s tempting to save money by picking up consumer-grade laptops, routers, and software, but this decision often backfires. What works fine for home users can cause major headaches in a business setting, leading to security risks, unexpected downtime, and higher costs in the long run.
Let’s examine why consumer-grade technology isn’t suited for business use and why investing in professional-grade IT solutions is smarter.
1. Reliability: Built for Homes, Not Businesses
Consumer hardware and software are designed for light use: checking emails, browsing the Web, and occasionally streaming. However, in a business, technology must handle multiple users, higher workloads, and constant uptime. Consumer products simply aren’t built for this level of demand.
For example, a standard home-grade router might work well in a house with a few connected devices, but in an office with dozens of employees, it could struggle to handle the traffic, leading to slow connections and frequent crashes.
Business-grade alternative. Enterprise routers, servers, and workstations are designed to handle continuous operation, meaning fewer breakdowns and more productivity.
2. Security Risks: Consumer Tech Lacks Proper Protection
Consumer-grade technology often lacks the advanced security features businesses need to keep sensitive data safe. Many home devices don’t have features such as multi-factor authentication, intrusion detection, or advanced firewalls, leaving your business open to cyberthreats.
Using consumer-grade security software is also risky. Many home antivirus programs don’t provide centralized control, meaning each employee is responsible for their own updates and scans, which is a recipe for disaster.
Business-grade alternative. Professional security solutions offer centralized control, encrypted storage, and advanced threat detection to protect your business.
3. No Centralized Management: A Nightmare for IT
Consumer hardware and software are designed for individual users, not teams. If multiple employees use different devices, managing updates, security settings, and software licenses can become a logistical nightmare.
For example, if employees use personal laptops with consumer operating systems, your IT team can’t easily push updates, enforce security policies, or monitor activity across the organization.
Business-grade alternative. Professional IT solutions allow for remote monitoring, automatic updates, and centralized management to keep everything running smoothly.
4. No Dedicated Support: When Things Go Wrong, You’re on Your Own
Most consumer-grade products come with basic support, usually in the form of email assistance or community forums. When a problem arises, you could be left waiting days or weeks for a response. Business-grade solutions come with priority support, service-level agreements (SLAs), and on-site repair options.
If your internet goes down or your office printer stops working, do you really want to rely on a call center with long wait times?
Business-grade alternative. Enterprise IT solutions offer 24/7 support, dedicated account managers, and fast on-site service to minimize downtime.
5. Limited Scalability: Consumer Tech Won’t Grow with Your Business
As your business grows, your IT infrastructure needs to scale with it. Consumer-grade solutions are built for fixed use cases and don’t offer the flexibility required for expansion.
For example, a consumer Wi-Fi setup might work fine for a small office, but as you add more employees, devices, and cloud-based applications, it could become a bottleneck.
Business-grade alternative. Scalable solutions allow you to expand storage, increase network capacity, and integrate new tools without replacing everything.
6. Shorter Lifespan: More Frequent Replacements
Consumer-grade hardware isn’t built to last. The components inside budget laptops, printers, and storage devices are typically cheaper and wear out faster, meaning more frequent replacements and higher long-term costs.
A business that relies on consumer-grade hardware may constantly replace failing computers or deal with unexpected breakdowns that disrupt operations.
Business-grade alternative. Professional devices last longer, offer better warranties, and allow for upgrades instead of full replacements.
7. Compatibility Issues: Consumer Tech Doesn’t Always Work with Business Systems
Many businesses rely on enterprise software, cloud services, and secure VPNs that aren’t compatible with consumer-grade devices. Using consumer-grade tech can create integration headaches, slow down operations, or lead to compliance issues in regulated industries.
For example, a business storing sensitive client data on a consumer cloud storage service might not be meeting legal security requirements, putting the company at risk of data breaches and fines.
Business-grade alternative. Professional IT solutions integrate seamlessly with enterprise software, cloud applications, and compliance standards.
8. Higher Long-Term Costs: Saving Money Today Can Cost More Tomorrow
The main reason businesses choose consumer-grade hardware and software is cost, but this short-term saving often leads to higher expenses in the long run. Frequent failures, security breaches, slow performance, and lack of support add to lost productivity and higher costs.
A cheap consumer laptop might seem like a good deal, but if it needs replacing every two years and slows employees down with crashes and lag, it’s not really saving you money.
Business-grade alternative. Investing in reliable technology reduces downtime, increases efficiency, and saves money over time.
Why Businesses Should Invest in Professional IT Solutions
At the end of the day, your business runs on technology. Using consumer-grade hardware and software creates more problems than it solves, from security risks to frequent downtime and hidden costs.
As a managed service provider, we help businesses such as yours choose the right technology, that which keeps you secure, efficient, and prepared for growth. Whether it’s upgrading your network, improving security, or managing IT support, we take the hassle out of technology so you can focus on running your business.
Need Better IT for Your Business? Let’s Talk
Don’t let consumer-grade tech hold your business back. If you want IT solutions that work for you, not against you, get in touch with us today.
Want to be notified when our next blog is posted, sign up here.



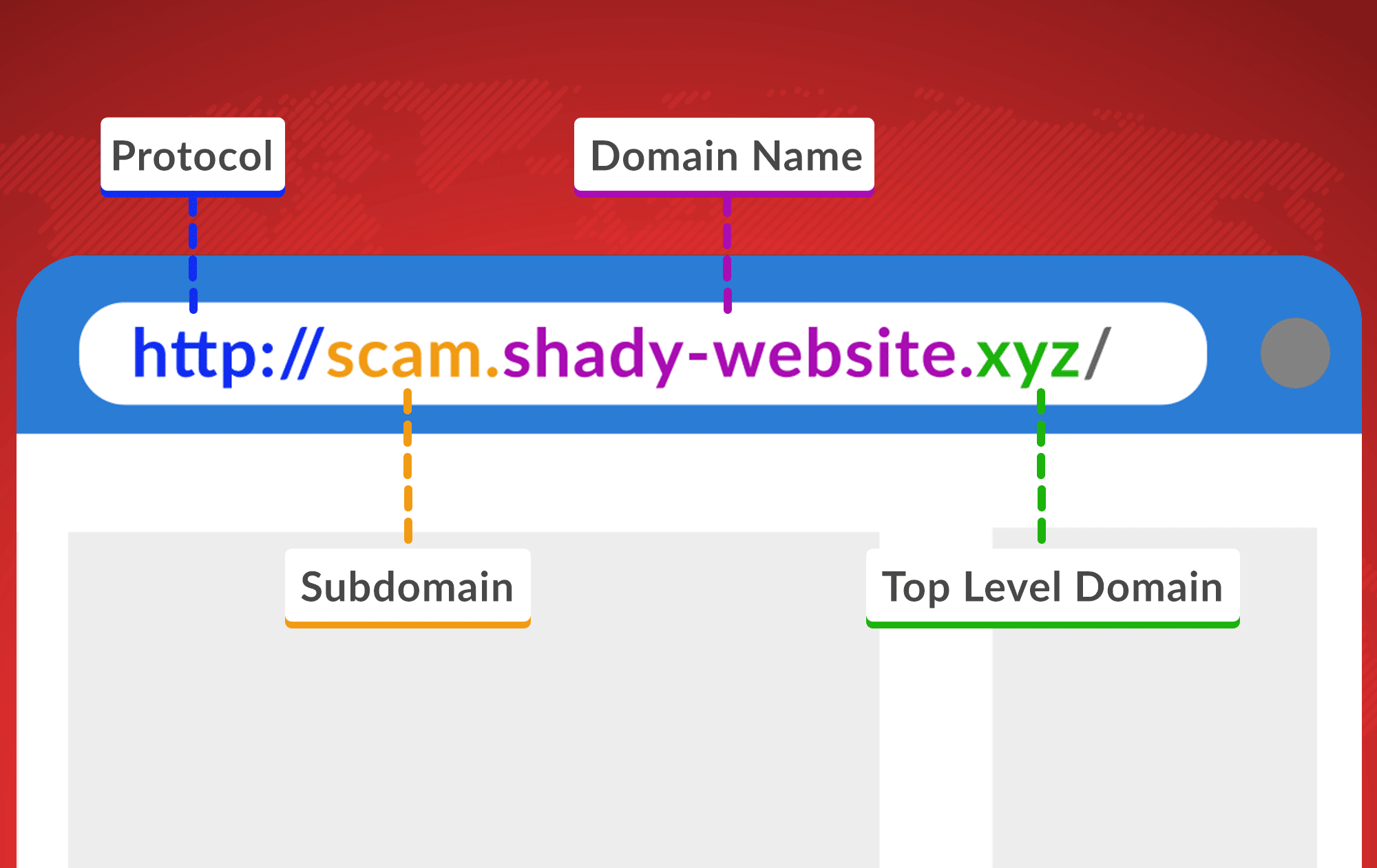
 Hackers Hide in the Hyperlinks: Spotting Malicious URLs
Hackers Hide in the Hyperlinks: Spotting Malicious URLs
 We’ve all been there: an unexpected tech glitch throws a wrench in your works at the worst possible moment. As annoying as it is, staying calm and providing full transparency with your IT friends will have you back up and running in no time.
We’ve all been there: an unexpected tech glitch throws a wrench in your works at the worst possible moment. As annoying as it is, staying calm and providing full transparency with your IT friends will have you back up and running in no time.
 If your trusty office PC has started showing its age, with more issues cropping up lately, you may be wondering if it’s finally time to say goodbye to your old friend. Or could some TLC in the form of repairs get it back in the game?
If your trusty office PC has started showing its age, with more issues cropping up lately, you may be wondering if it’s finally time to say goodbye to your old friend. Or could some TLC in the form of repairs get it back in the game?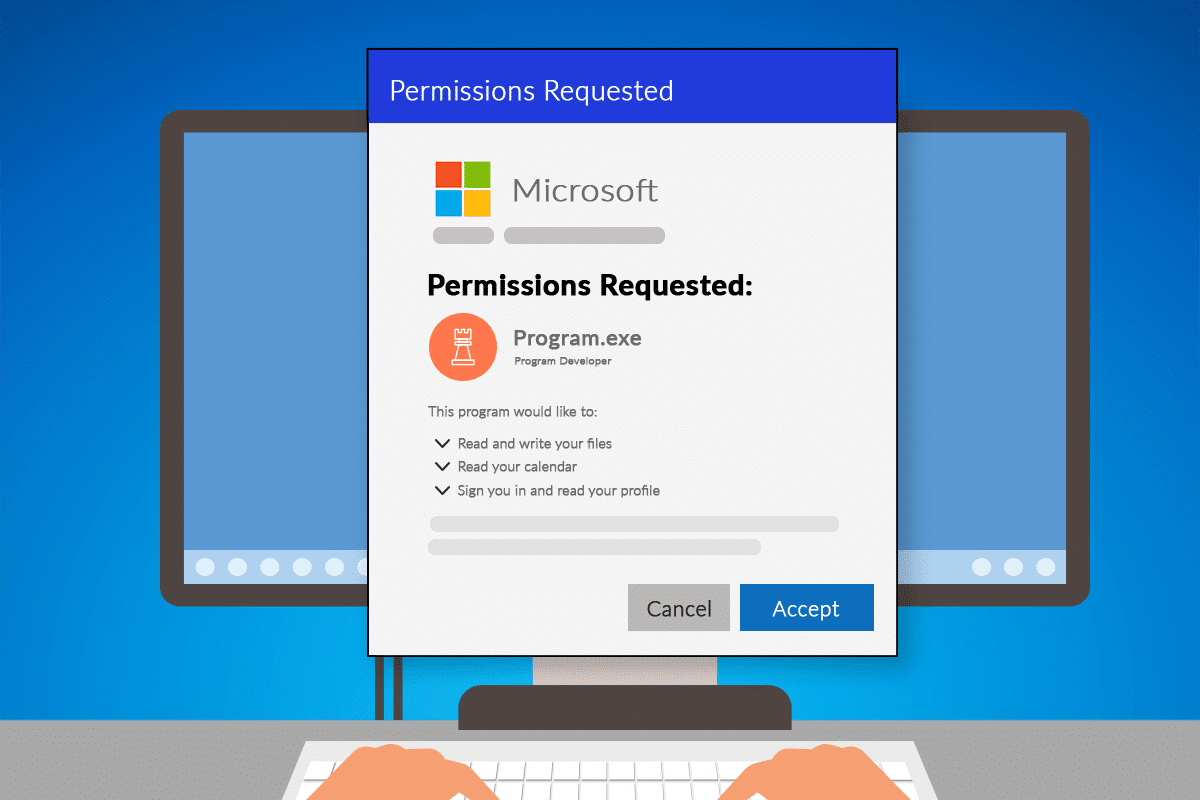
 If your business uses Microsoft 365 applications, you or your employees may have encountered a pop-up window requesting permission to access various account data.
If your business uses Microsoft 365 applications, you or your employees may have encountered a pop-up window requesting permission to access various account data.