Is It Worth Fixing My Aging Office Computer?
 If your trusty office PC has started showing its age, with more issues cropping up lately, you may be wondering if it’s finally time to say goodbye to your old friend. Or could some TLC in the form of repairs get it back in the game?
If your trusty office PC has started showing its age, with more issues cropping up lately, you may be wondering if it’s finally time to say goodbye to your old friend. Or could some TLC in the form of repairs get it back in the game?
We are often asked to help clients make this decision. Several important factors must be considered when determining the best path forward.
How Old Is It Really?
While it may seem like you just bought it yesterday, some computers have relatively short lifespans in technological terms. If your machine is more than 7 years old, it’s likely well past its prime. Parts can become difficult to source, and repair costs may exceed the original value.
What Issues Are Cropping Up?
Minor glitches that cause annoyance but don’t hamper use, such as a faulty keyboard, can often be fixed for $50-$150. On the other hand, multiple hardware failures, a dying motherboard, or other major component replacements indicate deeper underlying issues. For problems of that magnitude, repairs may run to 50%-75% of a new comparable model.
Will Parts Be Readily Available?
Specific key components may go out of production after a few years, especially with aging laptops. If it’s determined that your motherboard, screen, or other vital piece needs swapping out, there’s a good chance we won’t be able to get a replacement. This significantly increases repair costs and turnaround time, due to custom orders or used-part sourcing.
How’s the Performance Over Time?
Modern computing demands continue to grow exponentially with each passing year. If your PC has been steadily slowing down over the last 6-12 months and is struggling to run even basic tasks, it may be time for an upgrade.
What’s Your Budget Situation?
For clients on a tight budget, we’re always willing to thoroughly diagnose issues and provide affordable repair options to squeeze out a little more usability from an older machine. However, if an attractive new model is realistically within your means, an upgrade may give you several more years of smooth sailing.
Let’s Diagnose Your Situation
Rather than taking guesses, we always recommend bringing your computer for a thorough diagnosis. We can carefully assess its overall condition, identify any underlying problems, provide repair estimates, and help you weigh up the costs and benefits of fixing versus upgrading based on your unique needs and budget.
With the right solution, you’ll be back to enjoying your computer for many more years to come!
Want to be notified when our next blog is posted, sign up here.
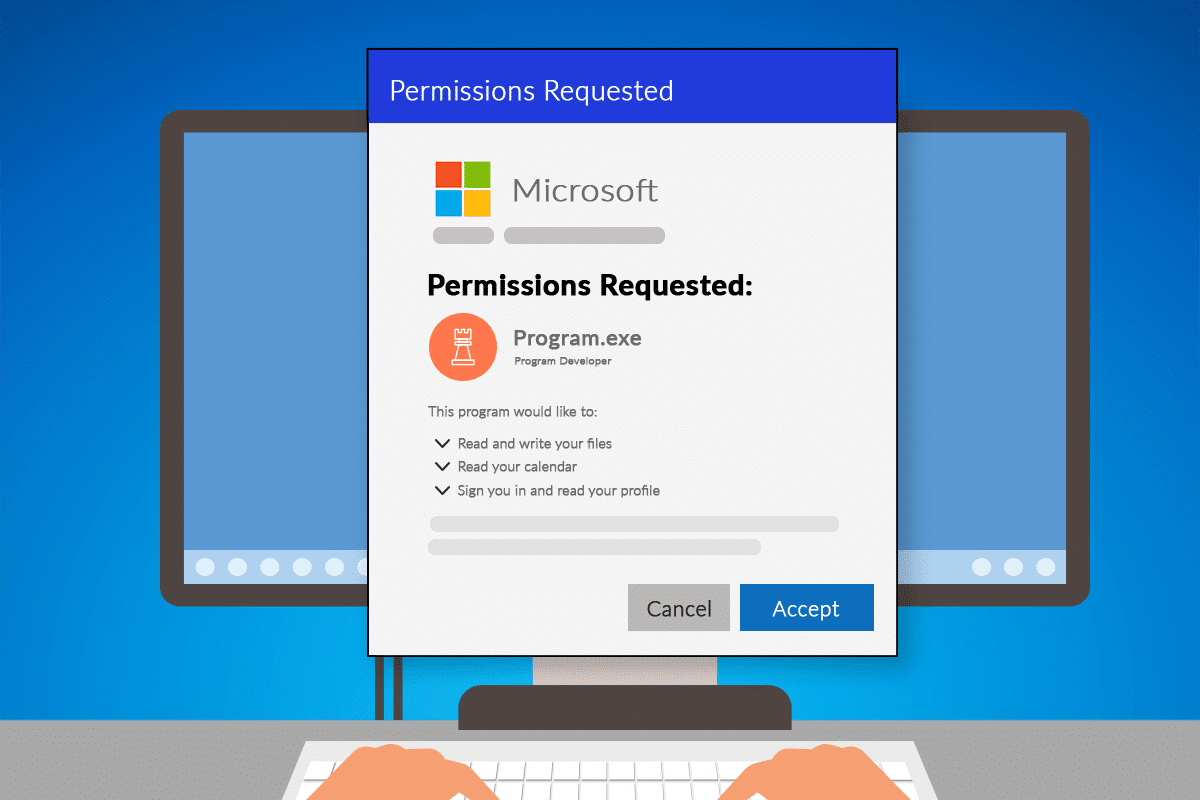
 If your business uses Microsoft 365 applications, you or your employees may have encountered a pop-up window requesting permission to access various account data.
If your business uses Microsoft 365 applications, you or your employees may have encountered a pop-up window requesting permission to access various account data.
 It’s a Wednesday afternoon, and you’ve just sat down to focus on an important project. But suddenly, you notice your internet connection isn’t working. A few minutes later, the printer on the other side of the office starts beeping with an error. Then, a pop-up appears on your computer saying your antivirus subscription needs to be renewed.
It’s a Wednesday afternoon, and you’ve just sat down to focus on an important project. But suddenly, you notice your internet connection isn’t working. A few minutes later, the printer on the other side of the office starts beeping with an error. Then, a pop-up appears on your computer saying your antivirus subscription needs to be renewed.





