Welcome to the ‘Internet of Things’
 You arrive at home and the door unlocks because it knows who you are, sensing the key in your pocket. The lights switch themselves on and your favorite music begins to stream gently through the living area. It’s already the perfect temperature, and as you head for the fridge, you notice an alert on the screen congratulating you on meeting your exercise goal today and suggesting a tasty snack.
You arrive at home and the door unlocks because it knows who you are, sensing the key in your pocket. The lights switch themselves on and your favorite music begins to stream gently through the living area. It’s already the perfect temperature, and as you head for the fridge, you notice an alert on the screen congratulating you on meeting your exercise goal today and suggesting a tasty snack.
Okay, it sounds like a scene from a movie, but it’s actually reality today thanks to the Internet of Things (IoT). Almost anything that can be turned on or off is now able to be connected to the internet. An entire industry has popped up to help users create a custom experience designed around their unique needs. Electronic locks, lights, healthcare wearables and household appliances are just the beginning. IoT goes beyond devices you can use to surf the web – it’s a global revolution.
Adapters can transform even the most random appliance into a connected gadget, as well as add new layers of functionality. Cloud software is creating piggy-back connections, resulting in not just a new experience, but a new way of interacting with the data produced. It may all seem impossibly futuristic, but IoT is less about technology and more about enhancing relationships between people-people, people-things and things-things.
Millions of people are wearing a Fitbit or Jawbone to track steps and calories, while others are letting their fridge order groceries! The practical applications are almost endless, commonly including: GPS trackers on pets, home security via webcam, patient monitoring of blood pressure/heart rate, weather monitoring, and remote power points. No more worrying all day if you left the iron on, just push a button on your phone and know for sure it’s turned off.
Of course, with all this connectivity comes risks. While the idea of having your toaster hacked is a bit mind-boggling, technology connected to the internet is open to exploitation. The webcam that allows you to monitor your pets may also allow other people to glimpse inside your home, but only if it’s not secured properly. Unfortunately, it only takes one small gap for a cyber-attack to get through, and once in, all connected devices are at risk.
Having your lights taken over by a far-away prankster may seem like a small risk, but gaps allow them into your computers, phones and tablets too. That’s the part the movies skip over – the networking protections that exist in the background, shielding against attacks.
Taking the time to properly secure your IoT device is essential to making sure you get the whole, happy future-tech experience. We’re big fans of IoT and can’t wait to see what comes next!
Got an IoT device? Give us a call at (416) 645-2469, (905) 667-0441 or email us to help you set it up securely.


 The best way to avoid a computer virus is by using common sense, but that doesn’t mean you’ll be safe from attack. Even the most careful user can find themselves infected in an instant and spreading the virus faster than a sneeze in flu season. It’s why antivirus software is still the first package we install on all systems – because you never know when you’ll be attacked. But should you choose free or paid antivirus?
The best way to avoid a computer virus is by using common sense, but that doesn’t mean you’ll be safe from attack. Even the most careful user can find themselves infected in an instant and spreading the virus faster than a sneeze in flu season. It’s why antivirus software is still the first package we install on all systems – because you never know when you’ll be attacked. But should you choose free or paid antivirus?
 Why? Here are the top 5 reasons to call in the networking professionals today:
Why? Here are the top 5 reasons to call in the networking professionals today:
 The Internet is growing and evolving so fast even the dictionary has trouble keeping up. Here are 12 suddenly common terms that are helpful to know.
The Internet is growing and evolving so fast even the dictionary has trouble keeping up. Here are 12 suddenly common terms that are helpful to know.
 The countdown is on for Windows Vista users. On 11th April 2017, Microsoft will cease all support and security patching, just like they did with previous Windows versions. Naturally, you’re rather attached to your current operating system and not exactly leaping for joy at this news!
The countdown is on for Windows Vista users. On 11th April 2017, Microsoft will cease all support and security patching, just like they did with previous Windows versions. Naturally, you’re rather attached to your current operating system and not exactly leaping for joy at this news!
 Business-class Features
Business-class Features
 Keep it cool: Your laptop has 2 sure ways of telling you when it’s too hot – the fan and auto-shut off. Each component in your laptop is generating heat, and the harder it’s working, the more heat each creates. The fan runs to blow that heat out the vent and keep the components cool enough to continue operating. Because there’s no clear temperature indicator, your fan volume is the best guide to monitoring laptop heat. While the laptop is working hard (and getting hot), the fan will spin faster and louder. It’s not uncommon for it to sound like a hair dryer at times! Help it out by keeping your fan vent clear of books, blankets, and other blockages.
Keep it cool: Your laptop has 2 sure ways of telling you when it’s too hot – the fan and auto-shut off. Each component in your laptop is generating heat, and the harder it’s working, the more heat each creates. The fan runs to blow that heat out the vent and keep the components cool enough to continue operating. Because there’s no clear temperature indicator, your fan volume is the best guide to monitoring laptop heat. While the laptop is working hard (and getting hot), the fan will spin faster and louder. It’s not uncommon for it to sound like a hair dryer at times! Help it out by keeping your fan vent clear of books, blankets, and other blockages.
 We repair many computers and laptops each week, but unfortunately this is often ‘closing the barn door after the horse has bolted’. Computers have a habit of dying at the worst possible time – like when an important project is due tomorrow, or before you copy family photos to a backup. We’ve combined our repair services with preventative measures to ensure this doesn’t happen to you. Our managed IT services can remotely take care of all the computers in your business, protecting you against both threats and system failure.
We repair many computers and laptops each week, but unfortunately this is often ‘closing the barn door after the horse has bolted’. Computers have a habit of dying at the worst possible time – like when an important project is due tomorrow, or before you copy family photos to a backup. We’ve combined our repair services with preventative measures to ensure this doesn’t happen to you. Our managed IT services can remotely take care of all the computers in your business, protecting you against both threats and system failure.
 You may not be storing military secrets or running a billion-dollar empire, but your business is still an attractive target for hackers. You need a firewall – a guard standing at the door of your network to stop the bad guys from getting in while still letting your staff come and go without interruption.
You may not be storing military secrets or running a billion-dollar empire, but your business is still an attractive target for hackers. You need a firewall – a guard standing at the door of your network to stop the bad guys from getting in while still letting your staff come and go without interruption.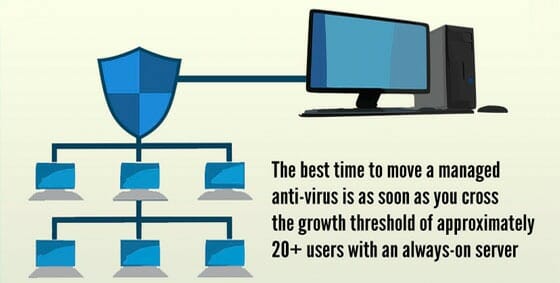
 Unfortunately, the biggest threat to your data and network security is your staff. Fantastic, loyal, hardworking people, who make occasional silly decisions. Even the innocent ones, like ignoring the virus software update that keeps popping up, requesting to download the latest protections. Your staff aren’t intentionally putting your systems at risk, but they are creating a weak link that exposes your business to attacks that may cost you thousands.
Unfortunately, the biggest threat to your data and network security is your staff. Fantastic, loyal, hardworking people, who make occasional silly decisions. Even the innocent ones, like ignoring the virus software update that keeps popping up, requesting to download the latest protections. Your staff aren’t intentionally putting your systems at risk, but they are creating a weak link that exposes your business to attacks that may cost you thousands.