How to Make Computer Issues A Thing of the Past
 We repair many computers and laptops each week, but unfortunately this is often ‘closing the barn door after the horse has bolted’. Computers have a habit of dying at the worst possible time – like when an important project is due tomorrow, or before you copy family photos to a backup. We’ve combined our repair services with preventative measures to ensure this doesn’t happen to you. Our managed IT services can remotely take care of all the computers in your business, protecting you against both threats and system failure.
We repair many computers and laptops each week, but unfortunately this is often ‘closing the barn door after the horse has bolted’. Computers have a habit of dying at the worst possible time – like when an important project is due tomorrow, or before you copy family photos to a backup. We’ve combined our repair services with preventative measures to ensure this doesn’t happen to you. Our managed IT services can remotely take care of all the computers in your business, protecting you against both threats and system failure.
Anti-virus always up-to-date: While many businesses have anti-virus software installed, they don’t often have the latest virus and threat definitions. These systems are at risk every minute they spend online, as the anti-virus simply will not pick up and stop an unknown threat.
New viruses and hacking threats arise every day, and there are entire companies dedicated to creating anti-virus updates to catch them. We can make sure your anti-virus definitions are always up-to-date, keeping your computer secure against even the newest viruses.
Software patches: Hackers like to spend their time figuring out new ways to break into computer systems. Software companies like Microsoft and Apple release regular patches to close these security holes. The patches are supposed to be applied automatically, but we often find that isn’t the case – patches didn’t download, were canceled or produced an error. Our services involve remotely checking that each patch has been applied successfully, and troubleshooting if required. As an added advantage, any time new features are packaged into an update, you’ll find them already installed for you.
Early failure detection: Some parts in your computer send out alarm bells when they’re about to die. Unfortunately, they’re not literal alarm bells (that would be too convenient), but information in the background that needs to be interpreted or manually checked. We can monitor these and advise repairs as required.
Data protection: Hard drives which store your information do eventually wear out, but they’re one of the parts that send out early failure warnings. We can monitor this and give you ample warning so that you have time to back up your important files. When it’s time, we’ll work with you to arrange drive replacement, making sure to either clone or re-install your operating system, whichever suits your needs best.
Tune-ups: Even the most cared for computer will slow down over time. Hard drives become cluttered, operating systems corrupt and ghosts of uninstalled programs still remain. We can remotely schedule and run a regular maintenance routine that will keep your system running in top condition and lightning speeds.
Our managed IT service happens entirely behind the scenes, so there is no disruption to your experience. You simply enjoy the benefits of having your own IT specialist team at one flat, low cost. You and your family continue to use your computer/s as normal, the only difference is problems are fixed BEFORE they happen and your system has the very best security against threats.
Give us a call at (416) 645-2469, (905) 667-0441 or email us and start with managed IT services today.


 You may not be storing military secrets or running a billion-dollar empire, but your business is still an attractive target for hackers. You need a firewall – a guard standing at the door of your network to stop the bad guys from getting in while still letting your staff come and go without interruption.
You may not be storing military secrets or running a billion-dollar empire, but your business is still an attractive target for hackers. You need a firewall – a guard standing at the door of your network to stop the bad guys from getting in while still letting your staff come and go without interruption.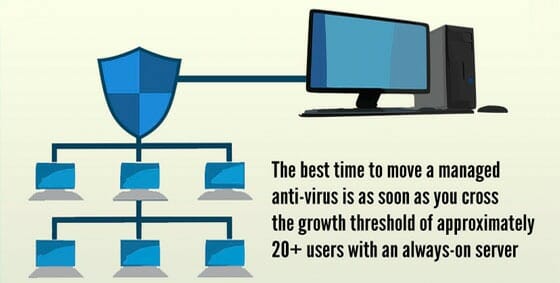
 Unfortunately, the biggest threat to your data and network security is your staff. Fantastic, loyal, hardworking people, who make occasional silly decisions. Even the innocent ones, like ignoring the virus software update that keeps popping up, requesting to download the latest protections. Your staff aren’t intentionally putting your systems at risk, but they are creating a weak link that exposes your business to attacks that may cost you thousands.
Unfortunately, the biggest threat to your data and network security is your staff. Fantastic, loyal, hardworking people, who make occasional silly decisions. Even the innocent ones, like ignoring the virus software update that keeps popping up, requesting to download the latest protections. Your staff aren’t intentionally putting your systems at risk, but they are creating a weak link that exposes your business to attacks that may cost you thousands.
 Remember the awe you felt when you turned on your new computer and it loaded in a flash? Your computer was the envy of your friends and you weren’t afraid to bathe in that glory. Button on, ready to go, those were the days!
Remember the awe you felt when you turned on your new computer and it loaded in a flash? Your computer was the envy of your friends and you weren’t afraid to bathe in that glory. Button on, ready to go, those were the days!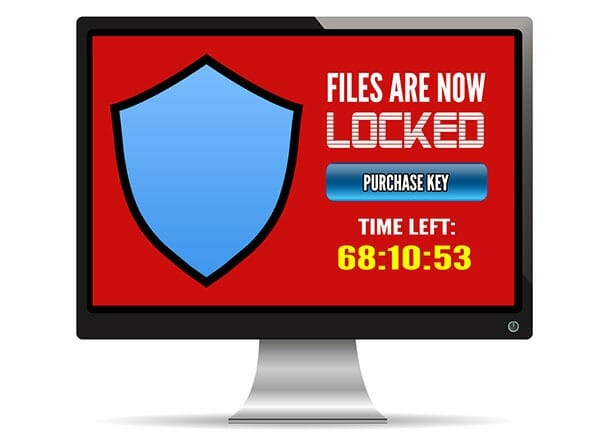
 Ransomware has undeniably been the biggest security threat of 2016. No-one was safe. Hackers targeted everyone and everything, including home PCs – and they were astoundingly successful – earning themselves upwards of $846million from US reported incidents alone. Business is booming for hackers, with thousands of attacks each day bringing in an average of $640 per target. Perhaps even more alarmingly, the financial cost of each individual attack is on the rise – the more ransomware proves to be an easy earner for them, the more they demand each time.
Ransomware has undeniably been the biggest security threat of 2016. No-one was safe. Hackers targeted everyone and everything, including home PCs – and they were astoundingly successful – earning themselves upwards of $846million from US reported incidents alone. Business is booming for hackers, with thousands of attacks each day bringing in an average of $640 per target. Perhaps even more alarmingly, the financial cost of each individual attack is on the rise – the more ransomware proves to be an easy earner for them, the more they demand each time.
 The message is clear: email is king. Many clients and customers choose to communicate primarily by email and as you know, it gives a fantastic ROI in your marketing strategy…unless you’re using a free email like Hotmail, Gmail, or even your internet provider. If that’s the case, you’re losing business each and every day.
The message is clear: email is king. Many clients and customers choose to communicate primarily by email and as you know, it gives a fantastic ROI in your marketing strategy…unless you’re using a free email like Hotmail, Gmail, or even your internet provider. If that’s the case, you’re losing business each and every day.
 There’s one thing all teens can do better than adults – and it’s not Snapchat. They’ve become experts at quickly locating information on the internet.
There’s one thing all teens can do better than adults – and it’s not Snapchat. They’ve become experts at quickly locating information on the internet.
 That pop up just won’t leave. It’s been hounding you to upgrade your software and clearly, it has zero intention of giving you a moment’s rest. That software wants to be upgraded and it wants it now.
That pop up just won’t leave. It’s been hounding you to upgrade your software and clearly, it has zero intention of giving you a moment’s rest. That software wants to be upgraded and it wants it now.
 People happily share their private information online, building robust libraries that can easily become a one-stop goldmine for fraudsters.
People happily share their private information online, building robust libraries that can easily become a one-stop goldmine for fraudsters.
 Every employee shares one inescapable flaw that is putting your business at risk.
Every employee shares one inescapable flaw that is putting your business at risk.